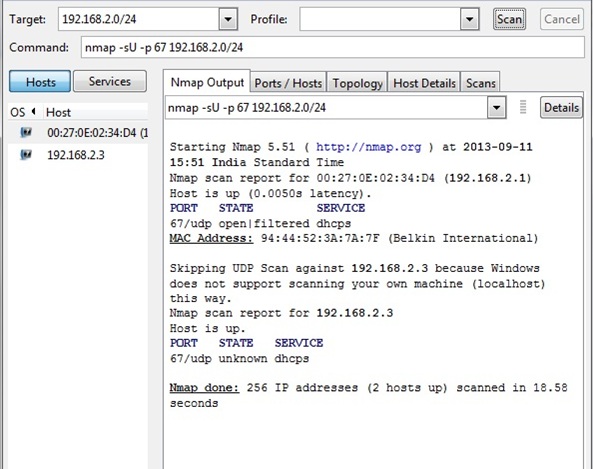
In this tutorial, the mechanism to detect a rogue dhcp server with nmap is understood. Rogue dhcp servers are setup on the network by attackers to create disruption of services. nmap is installed on a system. nmap is used to scan, UDP port 67, which is used by DHCP servers on the network. As the network administrator would be aware of the IP address of the DHCP server on the network, any other IP address associated with UDP port 67 would be identified as a rogue DHCP server. The following screenshot shows the command which can be used for scanning the network 192.168.2.0/24 for udp port 67. The output of the command returns the dhcp servers on the network. In this network, there is only one valid dhcp server, which is 192.168.2.1.The status of the port 67 is shown as open.
===================================================================================================================
This is a sample content from the below book
——————————————————————————————————————-
—————————————————————————————————————————————